Ways for Managing IP and Data Security When Outsourcing Software Development

Outsourcing involves sharing proprietary information with external entities, which creates vulnerabilities that malicious actors may exploit.
~ TPS Software
Do you find managing IP and data security challenging while outsourcing software development? Well, outsourcing is a strategic move for cost optimization and accessing specialized expertise. However, you need to be extra careful as you are sharing more than the mere project requirements.
Because, you should not leave the door wide open for:-
- IP theft or misuse
- Data breaches
- Reputational damage
Since the risks are not hypothetical, you cannot take a chance to lose the game! From keeping the legal and contract stuff right to ensuring your outsourcing software development is aligned correctly, it takes what it takes to minimize the risk.
Let’s jump to the write-up and find out how to manage your IP and maintain data security while outsourcing software development in 2025.
What Are Intellectual Property Rights?
Valuable assets for business that represent unique ideas, innovations, and creative works are Intellectual property. So, if you understand them properly, you will be able to safeguard your sensitive information and ensure a successful partnership while outsourcing.
It also helps you to have legal protection and avail recognition.
What Are the Data Security Risks Associated With Outsourcing Software Development?
Since outsourcing is a key skill to access specialized talent within a budget, it comes with potential data security risks. And, yes, you need to be vigilant about it!
So, you need to establish a robust and secure framework is a cornerstone of a successful partnership.
Here are the critical security risks that are associated with outsourcing software development:-
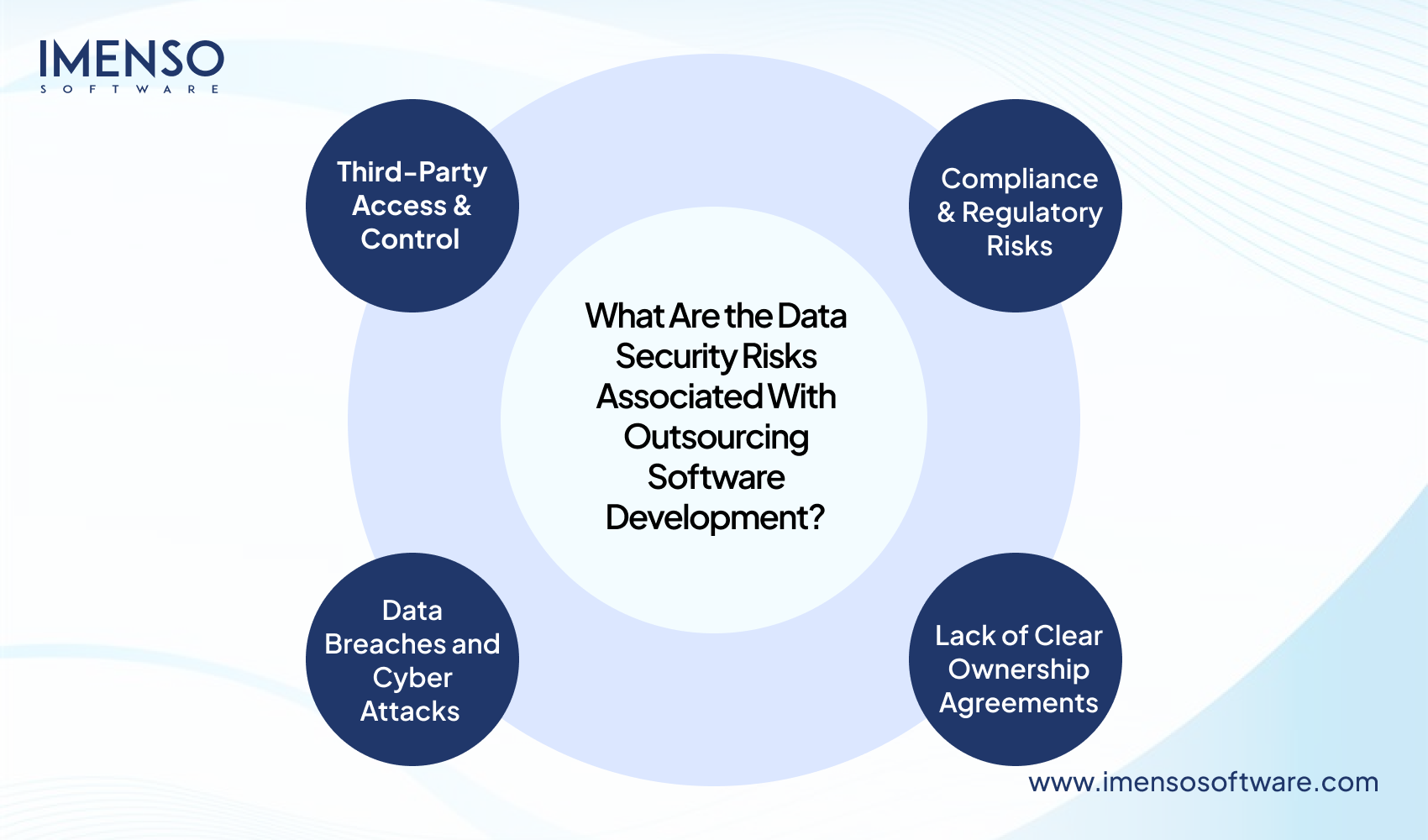
- Third-Party Access & Control
Third-party setups can introduce the risk of unauthorized access and data exposure. This is because your outsourcing partner may need to get access to your crucial business information to perform their services. So, you need robust access control and proper data segregation to minimize such data security and IP outsourcing.
- Data Breaches and Cyber Attacks
Since you have decided to outsource software development causes the addition of a few more points of vulnerability in the data flow, which increases the risk of data breaches. Consider what a weak link in your plan for outsourcing software development can do?
Well, it can lead to data theft, malicious activities, and much more.
And, to prevent it, you can:-
- Regular security audits
- Encryption
- Data backup strategies
- Compliance & Regulatory Risks
Have you encountered that different data protection laws and regulations can cause compliance risks? So, if you fail to adhere to industry-specific or international data compliance standards may result in legal consequences and reputational damage.
- Lack of Clear Ownership Agreements
Are you sure that you have explicitly defined the terms of your outsourcing agreement? If not, disputes over IP ownership may arise. This is very much a risk, especially when:
- The outsourced team dares to use your code for their projects.
- A contract won’t determine whether your derivative will work for you or not.
How to Navigate to IP Rights in Outsourcing Software Development?
Do you find it extremely difficult to protect an IP while doing software development outsourcing?
Although outsourcing software development can supercharge your business, it also comes with legal landmines. Chief among them? Intellectual Property (IP) rights. Who owns the code? What happens if your outsourced partner reuses your product idea or sells it elsewhere? These aren’t just “nice to know” details, but are critical to your business survival.
Jump to the strategies discussed here to know the IP Rights in outsourcing software development.
- Who is the owner of the software:
Openly disclose who is going to keep the rights to the software and the related work. Although it is unsaid that the other party, who is demanding the software or the owner, has the right, it is necessary to clearly say it in the contract.
- Shield Your Secrets: Secrets are meant to be kept, and you will have to make sure that both parties keep them safe.
- Be Careful Who Knows Your Secret: Don’t tell your secrets to everyone because it will help you avoid any accidental sharing or misuse.
- Include Your Free Software: Disclose any free software if you are using it. You need to follow the rules and make sure that it doesn’t cause any problems with owning the software you’re making.
- Checkups: Your contract should allow checkups to ensure that everyone follows the rules. It would help to spot and fix any problems early.
1. Why IP Protection Matters in Outsourcing
When you outsource software development, you’re not just hiring talent, you’re also handing over your ideas, concepts, and sometimes your entire product blueprint. This makes intellectual property protection one of the most critical concerns in any outsourcing relationship.
What Falls Under IP in Software?
IP software development includes:
- Source code
- Algorithms and logic
- Architecture diagrams
- UI/UX designs
- Technical documentation
- Business processes and trade secrets
These assets form the core of your competitive advantage, so losing control over them can be catastrophic.
The Risk Is Real
Without proper legal safeguards, an outsourcing partner could:
- Reuse your code for other clients
- Claim ownership of co-developed assets
- Leak or sell your ideas to competitors
When outsourcing software development, always clarify IP ownership. Without explicit terms, you may find yourself battling over rights to your product.
Why You Must Secure Ownership?
If you don’t clearly define IP ownership in your contracts, the default legal position might grant some rights to the developer, especially if they contributed creatively to the project. This can lead to lengthy disputes, rework, or even product delays.
Startups and SMEs, in particular, need to ensure that all rights are transferred to them as part of the agreement, not just the final product, but also the code, design assets, and future updates.
2. Legal Foundations: Contracts, NDAs & Ownership Agreements
Outsourcing without solid legal protection is like building software without version control; one mistake, and you could lose everything. Before any code is written, your first priority should be creating airtight legal agreements that clearly define rights, responsibilities, and remedies.
Key Documents You Need
- Non-Disclosure Agreement
Protects sensitive information like business plans, source code, and product ideas. Every developer, contractor, or partner must sign one. - Master Services Agreement (MSA)
Outlines the overarching terms of the engagement, including payment, timelines, responsibilities, and IP clauses. - IP Ownership Clauses
Clearly specify who owns the software, code, and any derivative works, not just at delivery, but throughout the project. - Work-for-Hire or Assignment Agreement
Ensure that any IP created by the outsourcing partner is automatically assigned to your company.
The contract should specify who will own the IP generated during the project. Generally, clients want to retain full ownership of the final software and any ancillary materials.
Pro Tips
|
Any software outsourcing arrangement should begin with strong legal agreements: NDAs, SLAs, and IP clauses must be airtight. Solid contracts aren’t just paperwork, they’re your first line of defense.
3. Securing Data Throughout the Development Lifecycle
Data security isn’t just an IT concern during outsourcing software development, but it’s a business-critical priority. Every phase of development, from ideation to deployment, involves handling sensitive data. Without proactive security measures, even trusted vendors can become a liability.
Security at Every Stage:-
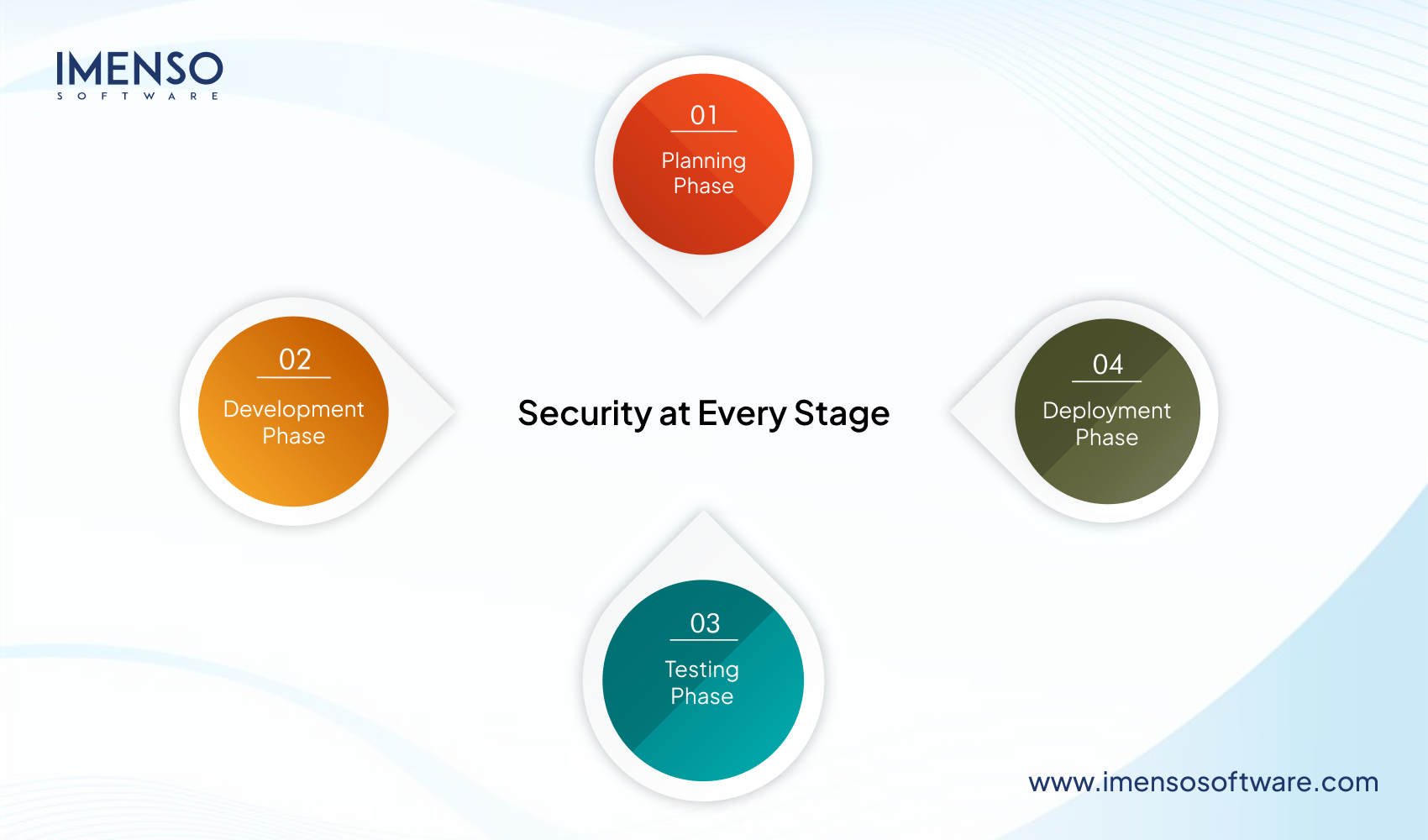
- Planning Phase
- Use secure file-sharing platforms for documents.
- Limit the exposure of proprietary business information until contracts are signed.
- Development Phase
- Enforce role-based access control to restrict who can view or edit your codebase.
- Use VPNs and encrypted channels for communication.
- Ensure development environments are isolated and comply with best practices.
- Testing Phase
- Sanitize test data to remove real customer or financial information.
- Use secure testing platforms and monitor third-party tool access.
- Deployment Phase
- Control access to live production environments.
- Run vulnerability scans and penetration testing.
Data security risks are heightened when third-party vendors are involved. Companies must assess how data is stored and accessed also transmitted during and after outsourcing.
Tools That Help
- GitHub/GitLab with 2FA – for secure version control
- AWS IAM Policies – for strict permission control
- Bitwarden or 1Password Teams – for secure credential sharing
- Slack Enterprise Grid or Microsoft Teams – for encrypted collaboration
Don’t Forget Compliance
If you handle sensitive user data or operate in regulated industries, ensure your outsourcing partner complies with:
- GDPR
- HIPAA
- SOC 2
- ISO/IEC 27001
You can outsource the work, but not the responsibility. You are still accountable for data protection, even when a third party is doing the development.
4. Access Control and Code Management
Once your project is underway, who has access to what becomes a defining factor in how secure your outsourced development truly is. The most skilled team can accidentally or intentionally create vulnerabilities without strict access control and code governance
Limit Access by Role
Implement role-based access control (RBAC) across all systems involved in the project:
- Developers get access only to what they need.
- Testers are isolated from production code.
- Project managers and stakeholders get read-only or restricted views.
This reduces the attack surface and minimizes the risk of data leaks or accidental overwrites.
Secure Code Repositories
Use trusted code management platforms (like GitHub, GitLab, Bitbucket) with:
- Two-factor authentication (2FA)
- Branch protection rules
- Audit logs to monitor commits and changes
Make sure external developers push code via pull requests and that you review and approve all merges.
Outsourcing creates opportunities for cybercriminals. Without strict access control and audit policies, your source code and data could be exposed.
Use Encrypted File Storage & Secure DevOps Tools
Ensure that:
- Source code is backed up in an encrypted version storage
- Access to cloud resources (like AWS, Azure) is secured through IAM policies
- CI/CD pipelines are configured to avoid exposing secrets or credentials
Revoke Access Promptly
When a developer leaves the project or changes roles, revoke or limit access immediately. Regular audits of user roles and permissions help prevent leftover accounts from becoming entry points for malicious activity.
5. Ongoing Monitoring and Compliance Checks
Protecting your IP and data isn’t a one-time task but an ongoing responsibility. Once your outsourced team is up and running, you must do continuous monitoring and regular compliance.
A. Real-Time Monitoring Tools
Implement monitoring solutions that track:
- Access logs for code repositories and cloud resources
- Unusual login patterns or IP locations
- Code changes outside scheduled hours
- Data transfer volumes and activity spikes
Use tools like:
- Datadog or New Relic for performance and usage monitoring
- Splunk for log analysis and security event detection
- AWS CloudTrail for tracking activity in cloud environments
Continuous monitoring is vital in outsourced development environments. If you’re not watching, you’re not protected.
B. Schedule Compliance Audits
Depending on your industry, you may be legally required to prove compliance with regulations such as:
- GDPR (for handling EU user data)
- HIPAA (for health tech)
- CCPA (for California consumers)
- PCI-DSS (if handling payment data)
Conduct quarterly or semi-annual audits to:
- Review access rights
- Validate encryption standards
- Ensure vendor-side security practices are still being followed
C. Document Everything
Maintain clear records of:
- Who accessed what and when
- What was changed in the codebase
- Any incidents and how they were resolved
- Signed agreements and compliance certifications
Trust, but verify. Transparency through documentation and audits is essential when outsourcing any data-sensitive function.
6. Best Practices Checklist for Securing IP and Data in Outsourcing
If you’re outsourcing software development, security and IP protection must be baked into every stage. Use this checklist to stay on track and protect your business from legal, financial, and reputational risks.
A. Before the Project Starts
- Choose a reputable vendor with a strong security track record
- Sign NDAs and IP ownership agreements before sharing details
- Include clear clauses in your contract for data protection and breach response
- Confirm the legal jurisdiction for IP disputes and enforcement
B. During Development
- Use role-based access control (RBAC) and limit permissions
- Keep all source code in secure, version-controlled repositories
- Use encrypted communication channels (e.g., Slack Enterprise, Signal)
- Implement CI/CD pipelines with controlled access and secret management
C. Ongoing Oversight
- Monitor activity with audit logs and real-time alerts
- Perform regular security audits and compliance checks
- Revoke access immediately when roles change or developers exit
- Stay updated with regulatory requirements (GDPR, HIPAA, etc.)
D. Strategic Habits
- Treat outsourcing as a partnership, not a hand-off
- Build redundancy and fallback options into your process
- Maintain thorough documentation of all assets and decisions
- Educate internal stakeholders about their security responsibilities
Following best practices in outsourcing isn’t just about reducing risk; it’s about building a stronger, more resilient business.
Build Smart, Stay Secure
Do you agree that outsourcing software development can be a game-changer? Whereas, it should never come at the cost of your intellectual property or data security. Let’s face it: in a world where data breaches and stolen code are becoming all too common, protecting your digital assets is essential to staying ahead.
The good news? You don’t have to choose between growth and security. Because you can work with external teams confidently, knowing your IP is safe every step of the way. It usually has solid contracts, a secure development process, and a bit of hands-on involvement.
Outsource smart. Secure early. Monitor always.
Want more information about our services?
Similar Posts

Custom Software Development vs. Off-the-Shelf Solutions: What’s Right for Your Business?
The tools and strategies a company employs often determine its ability to navigate challenges and scale effectively. For businesses aiming to redesign their software to better align with their goals, a crucial question arises: Should you opt for custom software development or adapt an off-the-shelf solution? Both options come with unique strengths and weaknesses. Choosing […]...

Node.JS Vs Python: Pick the Best Backend Technology in 2022
The battle between Node.js and python for the best backend technology is always on. One is old and established while the other one is new and trending. Which will win the war? Let’s dive in. Picking the right technology stack is pivotal for a web application project. The frontend and backend technology combination decides the project cost, […]...

Why MERN Stack is the Best Choice for Your Next Web Development Project
In today’s rapidly evolving digital landscape, choosing the right technology stack for your web development project is crucial. A well-rounded stack should offer efficiency, flexibility, scalability, and a supportive community. Among the various options available, the MERN stack stands out as a powerful and popular choice. Comprising MongoDB, Express.js, React.js, and Node.js, the MERN stack […]...